Sep 25, 2019 As we have seen, the macOS.GMERA malware writes a persistence agent to /Library/LaunchAgents. If you were manually threat hunting on macOS, a newly written LaunchAgent would immediately cause you to investigate further, and the same can be true for automated responses. We also saw that in the case of the GMERA malware, the parent process.
14 total Zoom Vulnerably / Exploit variants and a RCE Remote Code Execution found!
Just when you had enough of the first Zoom Vulnerably, Apple released MRTConfigData 1.46 (now 1.47!) to deal with 14 total variants and a Remote Code Execution (RCE) . I created this Index of MRT Links & Info to help you get through the confusion.
Jonathan Leitschuh reported the first vulnerably in Zoom. I wrote an article talking about this and how to remediate the RCE and Conferencing Video Bug here.
UPDATED: 07/18/19 – MRTConfigData 1.47 released and 3 more Zoom variants! Brings the total to 14.
MRT Malware Removal Tool Index
- 1. List of zoom opener variants and MRT versions
- 2. MRTConfigData Compatible OS versions.
- 3. Software Update & MRT Commands
- 4. Malware Removal Tool Documentation
- 5. Caveats of installing MRTConfigData and how the MRT scan works differently in 10.14 vs 10.13
- 6. Other ways to install MRT updates
- 7. Digging into the MRT Binary
- 8. More questions, Problems and Errors
- 9. Links to scripts and other MacAdmin articles
- 10. Disclaimer
1. List zoom opener variants and MRT Versions
How do we even know which variants are included in MRTConfigData v1.45 and v1.46? (Now 1.47!) The only way to find out is to dig into the MRT Binary Code. I talk about how I found the new variants a little more in section 7 below.
We now have 14 new Zoom Opener variants to worry about. Each one is a hidden folder listed in your user folder!
MRT Versions
- 1. MRTConfigData v1.45 – 7/10/19
- 2. MRTConfigData v1.46 – 7/16/19
- 3. MRTCOnfigData v1.47 -7/18/19
Zoom Variants
- 1.
/.zoomus– 1.45 - 2.
/.ringcentralopener– 1.46 - 3.
/.telusmeetingsopener– 1.46 - 4.
/.btcloudphonemeetingsopener– 1.46 - 5.
/.officesuitehdmeetingopener– 1.46 - 6.
/.attvideomeetingsopener– 1.46 - 7.
/.bizconfopener– 1.46 - 8.
/.huihuiopener– 1.46 - 9.
/.umeetingopener– 1.46 - 10.
/.zhumuopener– 1.46 - 11.
/.zoomcnopener– 1.46 - 12.
/.earthlinkmeetingroomopener– 1.47 - 13.
/.videoconferenciatelmexopener– 1.47 - 14.
/.accessionmeetingopener– 1.47
2. MRTConfigData Compatible OS versions.
You can run the MRTConfigData update on the following macOS versions.
- Mojave 10.14
- High Sierra 10.13
- Sierra 10.12
- El Capitan 10.11 (Note: You can only use
softwareupdate -ia --backgroundas the--include-config-dataoption was new in Sierra 10.12)
3. Software Update & MRT Commands
Let’s get right to it, here are the commands again if you want to remediate right now!
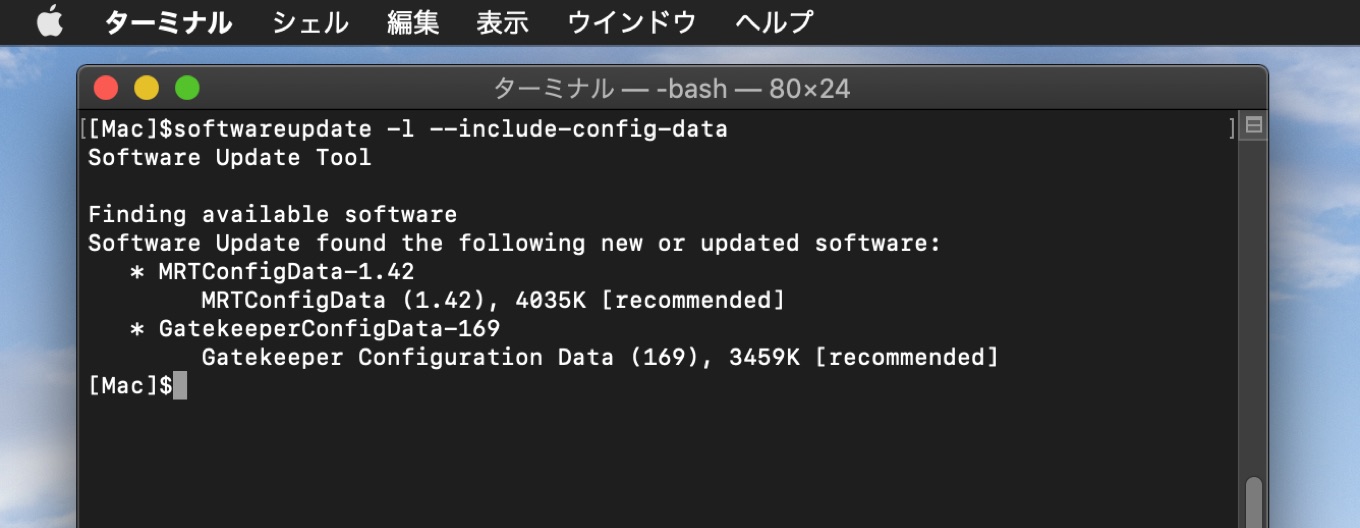
- 1. Check for config data updates:
/usr/sbin/softwareupdate -l --include-config-data - 2. Manual Install of MRT v1.47:
/usr/sbin/softwareupdate -i MRTConfigData_10_14-1.47 --include-config-data - 3. Verify Version of MRT:
/usr/bin/defaults read /System/Library/CoreServices/MRT.app/Contents/Info.plist CFBundleShortVersionString - 4. Force Run MRT.app in Agent mode:
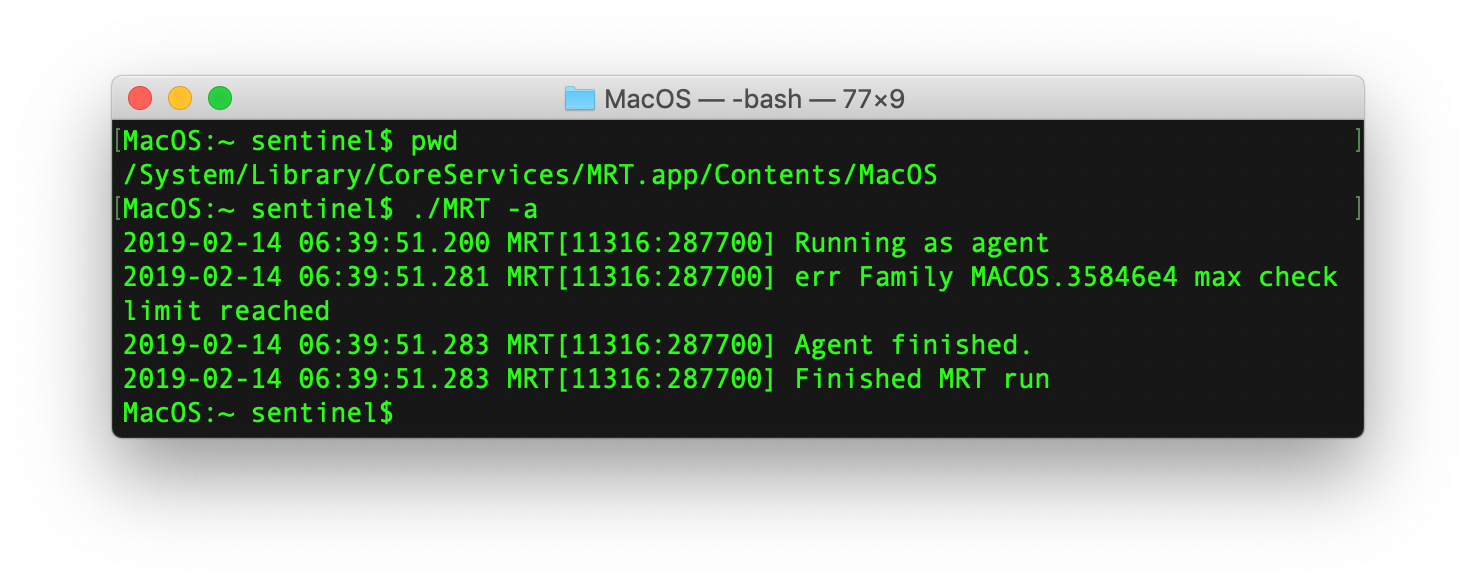
/System/Library/CoreServices/MRT.app/Contents/MacOS/MRT -a
If MRT finds Zoom the manual scan will look like this.
4. Malware Removal Tool Documentation
Apple has not documented how the MRT Scan works. The MRT Tool is called out with just a few lines in the macOS Security Overview for IT.
Apple refers to MRT updates as “Silent or Quiet Update” when referenced in the media. The MRT Binary doesn’t have a MAN page or a -help section. Targeted malware variants are not documented. Sounds like a job for #MacAdmins!!!
5. Caveats of installing MRTConfigData and how the MRT scan works differently in 10.14 vs 10.13
You need to know about a few caveats with this process. I have tested the installation and scan multiple times and found differences in each OS! Let’s start with Mojave 10.14 then move to High Sierra 10.13.
MRT in Mojave 10.14.5
- When you manually install the
MRTConfigDataupdate the MRT.app will automatically run a MRT Scan! - You only have to worry about other users who may have installed any of the opener variants as the MRT Scan only runs for the logged in user only.
- A restart and Logout/Login will kick off a manual MRT Scan.
- You can run a script that Rich wrote that will remove zoom from all logged in users.
MRT in High Sierra 10.13.6
- A reboot will kick of a MRT Scan
- A logout and login will kick off an MRT Scan
- When you manually install the
MRTConfigDataupdate the MRT Scan will NOT run automatically!!! - You will need to run the MRT.app agent scan manually to remove any zoom variants.
TLDR: Installing MRTConfigData in 10.14 automatically kicks off the MRT.app scan, while in 10.13 the MRT scan does NOT run automatically.
H/T to @howardnoakley and @alvarnell for pointing out that after installing MRTConfigData the MRT Scan kicks off automatically. I did not know it at the time but they were testing in 10.14. All my testing was on 10.13, so thats why I was getting different results!
6. Other ways to install MRT updates
If you are on Mojave 10.14.5 you will automatically get the MRTConfigData update as long as you have the following SoftwareUpdate Settings set to ON.
As long as you have these settings set to ON your Mac should automatically check in for new updates and install them every 24 hours.
For the com.appleSoftwareUpdate.plist file you need the following settings set to ON.
/Library/Preferences/com.appleSoftwareUpdate.plist
AutomaticCheckEnabled = 1AutomaticDownload = 1ConfigDataInstall = 1CriticalUpdateInstall = 1
If you want to install all background updates now without waiting you can issue the following command.
sudo softwareupdate --background --include-config – Only background updates
or
sudo softwareupdate -ia --include-config-data – Background updates AND OS level Updates
NOTE! The -ia option will install ALLavailable software updates including Combo, Safari and Security Updates.
The above commands will only install Xprotect updates if you have all the automatic software update settings set to ON.
7. Digging into the MRT Binary
Apple does not list the targeted malware variants anywhere, so the only way to find them is to dig into the MRT Binary Code. You cant just open the code inside MRT as it has thousands of lines of code. You have to first compare the current version to the old one. This will give you the first clues, as each piece of malware is given a code. In this case it was MACOS.354c063.
Now that we have the Malware Family ID we can then search the MRT Binary using a disassembler application. A disassembler like Hopper is used to view the actual code of the new MRT binary.
8. More questions, Problems and Errors
We still have questions about how the MRT works especially the MRT -d or daemon mode. I have even reached out to Apple for an answer on this.
Howard Oakley wrote a great article looking into this.
This is the best information we have so far.
Problems and Errors
Trying to run a manual update and scan can cause some problems in certain situations.
Macos System Library Core Services Mrt.app Contents Macos X
- 1. Running
/usr/sbin/softwareupdate -i MRTConfigData_10_14-1.47 --include-config-datashows
Macos System Library Core Services Mrt.app Contents Macos 7
If this happens run /usr/sbin/softwareupdate -l --include-config-data first.
- 2. Running the MRT Scan from a script shows
MRT ScanfailedToReceiveProfileList
You will need to run MRT in 10.14 as the logged in user.
9. Links to scripts and other MacAdmin articles
- CVE-Numbers
- DOS Vulnerability — Fixed in Client version 4.4.2 — CVE-2019–13449
- Information Disclosure (Webcam) — Zoom —CVE-2019–13450
- The Zoom Client before 4.4.53932.0709 on macOS allows RCE remote code execution – CVE-2019-13567
- Apple.com – About background updates in macOS Mojave Your Mac automatically installs background updates for the security configuration and data files used by macOS. – support.apple.com/en-us/HT207005
- Apple.com – macOS Security Overview for IT – 2018 – apple.com/business/resources/docs/macOS_Security_Overview.pdf
- Jonathan Leitschuh – twitter.com/jlleitschuh – Medium.com – A vulnerability in the Mac Zoom Client allows any malicious website to enable your camera without your permission. The flaw potentially exposes up to 750,000 companies around the world that use Zoom to conduct day-to-day business. – medium.com/bugbountywriteup/zoom-zero-day-4-million-webcams-maybe-an-rce-just-get-them-to-visit-your-website-ac75c83f4ef5
- Howard Oakley – twitter.com/howardnoakley – eclecticlight.co – Howard really dug into this when it first came out writing multiple articles on the zoom exploit. He also has multiple applications that he wrote that will help you, including one called SilentKnight that will tell you if all your XProtect definitions are up to date.
- Rich Trouton – twitter.com/rtrouton – derflounder.wordpress.com – Rich has written the best script yet to remediate the Zoom venerability on all user accounts.
- Karan Lyons – twitter.com/karanlyons – Github
- Fix for Zoom, RingCentral, Zhumu (and possibly more) RCE vulnerabilities – gist.github.com/karanlyons/1fde1c63bd7bb809b04323be3f519f7e
- Assetnote.io – Deep dive on how the RCE and Zoom exploit works. blog.assetnote.io/bug-bounty/2019/07/17/rce-on-zoom/
- Jamf Nation Discussion Forum – Zoom Exploit – jamf.com/jamf-nation/discussions/32561/zoom-exploit
- My article on the Zoom Exploit – mrmacintosh.com/how-to-remediate-the-zoom-vulnerability-with-apple-malware-removal-tool
/system/library/coreservices/mrt.app
- TheVerge.com – theverge.com/2019/7/8/20687014/zoom-security-flaw-video-conference-websites-hijack-mac-cameras
- Blue Jeans Response – support.bluejeans.com/s/article/BlueJeans-Detector-Service
- Macadmins.slack.com – You can also talk about the Zoom Vulnerability and join the #zoom channel or #security in MacAdmins Slack.
10. Disclaimer
I tried to test and research as much as possible to save you time. I hope this Index of MRT Links & Info helps you, but since this issue revolves around security please double check and test before you deploy. After deployment check again that the files inside the opener are in fact deleted.
Macos System Library Core Services Mrt.app Contents Macos 10
Index of MRT Links & Info